Docker Scout
Security superpowers for fearless innovators
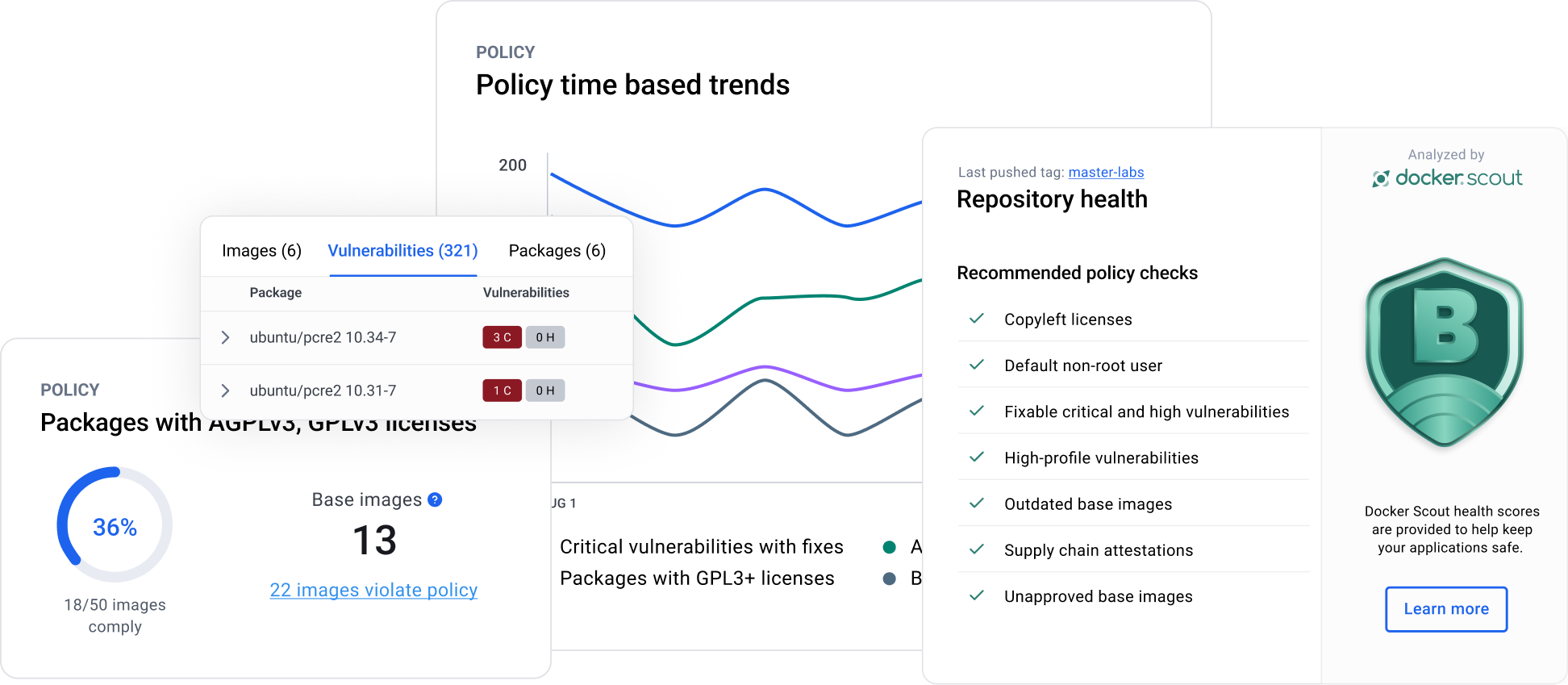
Unlock a new level of trust and visibility
Local Vulnerability Analysis
Identify security risks within your images before deployment
Docker Scout’s local vulnerability analysis scans your images for potential security issues before they reach production. By detecting vulnerabilities early, it helps you ensure safer deployments and reduce the risk of security breaches in your applications.
Image Remediation
Quickly address and fix security issues in your images
Docker Scout’s image remediation feature allows you to swiftly resolve security issues detected in your images. This capability streamlines your development process, maintaining high standards of software security and efficiency.
SDLC Integrations
Secure your SDLC from start to finish
Seamlessly integrate Docker Scout into your software development lifecycle (SDLC) with robust integrations. This feature ensures that security checks and analysis are embedded into your development process, providing continuous protection and efficiency.
Policy Evaluation
Evaluate and enforce security standards
Docker Scout’s policy evaluation tools help you ensure compliance and assess the security posture of your images against established guidelines.
“Docker Scout helps us ensure that our payments and user data are fully secured.”
Milen Dobrev
Senior Engineering Manager, Distilled
Frequently asked questions
Who can enable Docker Scout for my organization?
You must be an admin for the organization to enable Docker Scout.
Will remediation suggestions change depending on which layer is vulnerable?
If your base image has a security concern, Docker Scout will check for updates and patches to suggest how to replace the image. If issues exist in other layers, Docker Scout will reveal precisely where it was introduced and make recommendations accordingly.
How is Docker Scout using an SBOM?
An SBOM, or software bill of materials, is a list of ingredients that make up software components. Docker Scout cross-references SBOMs with streaming CVE data to surface vulnerabilities (and potential remediation) as soon as possible.
What makes Docker Scout different from other tools?
Competitors, if they offer remediation guidance at all, miss the mark on their limited scope of application security posture within the software supply chain, and often limited guidance when it comes to suggested fixes. Competitors have either limitations on runtime monitoring or no runtime protection at all. When they do offer runtime monitoring, it’s limited in its adherence to key policies. Competitors offer a limited scope on policy evaluation for Docker-specific builds.
How can I enable Docker Scout on remote images, registries, and artifacts in Docker Hub?
Docker Scout requires a Docker Hub organization. Learn more about configuring Scout for your registry in our technical documentation.
Secure your software supply chain at the source
Additional resources
Watch the demo
Explore Docker Scout’s capabilities in action by watching our demo. See firsthand how our solution integrates with your development environment and enhances your security posture.
Learn more
Join our community
Join the Docker community to connect with other developers, share knowledge, and get support. Engage in discussions, contribute to projects, and be part of a vibrant ecosystem.
Learn more
Read the blog
Keep up with the latest Docker news, tips, and best practices by reading our blog. Stay informed about new features, case studies, and industry trends.
Learn more
Find resources
Explore a wealth of resources including webinars and white papers. Equip yourself with the knowledge and tools needed to make the most of Docker.
Learn more